Key Highlights:
✅ XC-20 token standard on The X-Chain
✅ Contract language: solidity and lua
✅ Zero gas fees for $XCUR (XC-20)
✅ Curate’s private blockchain
✅ Near instant transactions
✅ Cross-chain compatible
✅ Seamless in-app UX
✅ Hybrid Consensus
✅ 20,000 TPS
✅ Live in June
Simultaneously launching along side and in-built The NFT Marketplace App in June 2021
XCUR (XC-20)
“To provide a scalable gasless marketplace, PoW will not cut it.” — James Hakim, Founder & CEO of Curate Group Ltd.
The security of a PoW network depends on the collective hash power of the network. A group of malicious entities could easily attack a small network and change the blockchain, while still playing by the rules of its protocol. This malicious group would just need a higher hash power. Unlike bitcoin, a small network is not massively distributed, and hence the hash power is far too low to provide any significant protection.
This is why we’ve started development on our hybrid chain ‘The X-Chain’, which benefits from both the advantages of PoW and PBFT.
From launch (June 2021), The X-Chain will be interoperable with XCUR ERC-20 and BEP-20 allowing seamless in-app integration. Alongside this will be our own blockchain explorer, available on the web.
Furthermore, The X-Chain will support future project integrations and interoperability with other chains as we continue to strike key partnerships to grow the user case of XCUR.
1. PBFT/PoW Hybrid
A PoW/PBFT-like consensus protocol, replaces the reliance on PoW by using endorsements, and hence is a solution to the aforementioned problem. Fundamentally, a new block can be added to the chain after having been agreed to, and endorsed by a given number of known peers. The chain can then be validated by checking the validity of the endorsement signatures.
There are 2 tiers of participants in such a network: External clients (such as software wallets and exchanges), who only have permission to submit transactions and audit the blockchain; And known peers, which will have the permission to create, endorse and commit blocks to the chain.
PBFT = Practical Byzantine Fault Tolerance
PoW = Proof of Work
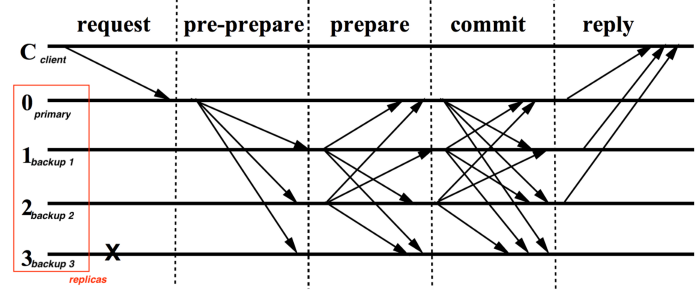
This solution, I believe, will not only protect from the mentioned type of attacks but will also allow a much higher transaction throughput. Transactions per second will only be limited by blocksize and network communication speed; While practical confirmation times should be more like those of VISA than of Bitcoin. Proof of Work chains require time & difficulty to confirm transactions, whereas we will rely on endorsements. (much faster)
2. The Life Cycle of a block in the endorsement model
To understand this model, its beneficial to look at the life cycle of each block as it goes from creation to inclusion in the blockchain…
In our current proof of work system, the life cycle of the block is relatively simple, It is created and mined, then distributed to all other peers. The hybrid model’s method of consensus is slightly more complex.
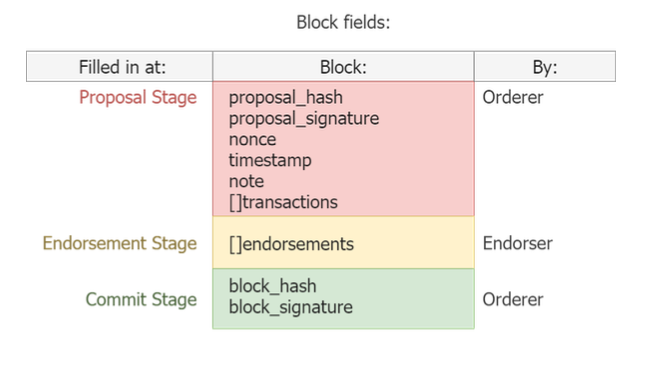
Each block in this model will go through three stages: A Proposal stage, where the block is created, mined (at a low difficulty) and signed by the orderer, this block is then distributed to all other known peers (called endorsers); The second stage is called the Endorsement stage, each endorser will check the proposal block is fully compliant with a given ruleset and the latest chain state, and then (if valid,) will return, to the orderer, an endorsement.
Endorsement [64]byte = signed(proposal_block_hash)
In the third and final stage, the Commit stage, the orderer waits until it has received at least X valid endorsements. The proposal block is then combined with the Endorsement signatures and the final hash is created.
X >= number_of_peers/2
Final_hash [64]byte = sha256(endorsements + proposal_hash)
This completed block is then distributed to all peers so that they can update their local state of the blockchain. At this point all transactions in the blockchain can be considered fully processed and valid.
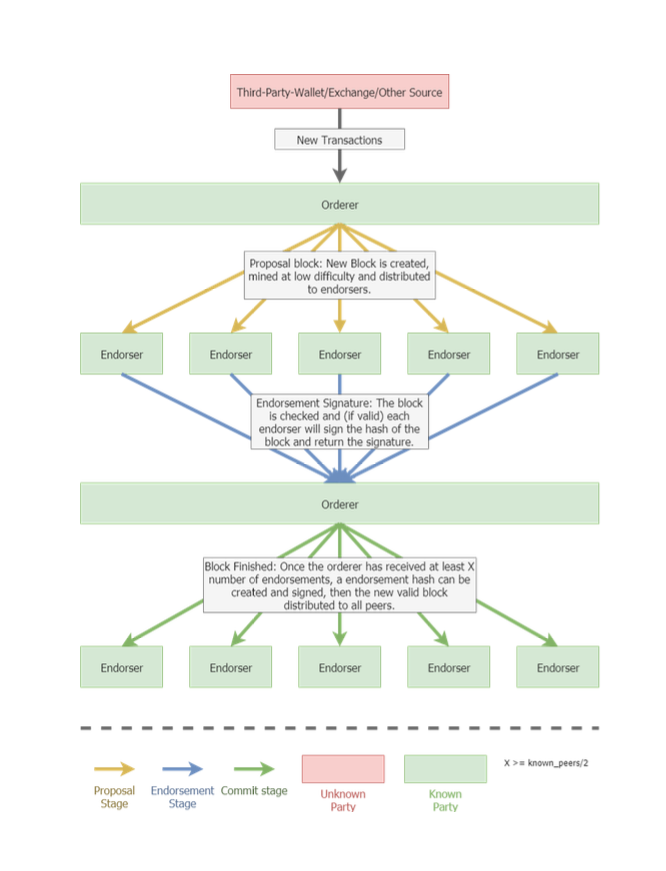
It’s important to note that each peer in the network including the orderer, must be polymorphic. This is to ensure that if the orderer is malicious or faulty, any other peer in the network can adopt that role to prevent any downtime.
3. Legacy Protection of the blocks using proof of work
On the surface, the endorsement model would work without any mining at all. Consensus can be reached even with X-1 faulty nodes. But, given a situation with X + 1 faulty/malicious nodes, the history of the blockchain could theoretically be rewritten at a hyperfast rate using a ‘consolidation’ attack (where networking times would be eliminated). To protect against this and other attacks, blocks can be mined at a low difficulty, adding a proof of work barrier to attacks, without significantly slowing down the throughput of the blockchain.
4. Updates to the protocol
The general transaction processing protocol will remain the same, however, extra rules and exceptions will be added for the proposal, endorsement and commit stages.
- Proposal hash is added. It will be the hash of all transactional data, timestamp, block notes, public key of the known orderer, and nonce. (This hash must be the solution to the target difficulty) BLAKE2B
- An array of endorsement signatures not included in the proposal hash. Each endorsementsignaturewillbedigitallysignedproposalhash.E CDSA
- Block hash. This is the hash of the proposal hash and the endorsements. B LAKE2B
- Orderer signature. This is the signed block hash matching the public key that first signed the proposal. ECDSA
- All signatures must come from a known and non-blacklisted Peer.
- The previous hash included in the proposal block will reference the last block’s final hash.
5. Known Peers and the Blacklist
For now, this is a permissioned, private blockchain. Known peers are trusted nodes that we want to interact with the function of validating and appending the blockchain. In essence, a list of known peers is merely a collection of public keys, which are publicly available.
Initially, the note in the genesis block should contain a list of all known peers. Signatures used on/within the block will be checked to see if they match one of these known peers. This prevents any unknown and untrusted party from participating.
A mechanism may be adopted to allow known peers to be added at a later point in time to increase the practical fault tolerance/flexibility of the network. However, this mechanism itself must be secure, because if it’s improperly handled, it could become a single point of failure. There are a few options for adding and blacklisting peers, which may be used exclusively or interchangeably:
Voting — A new known peer is voted in, with its inclusion in a block’s note, requiring X endorsements. This mechanism can also work for blacklisting a peer. I recommend this method.
Centralized protocol update — peers can be hard coded into the protocol and distributed through a secure centralized mechanism.
6. Future Update Flexibility
Updates to the protocol can be distributed through manual software changes, much like bitcoin core. As long as you keep an accurate account of the block indexes (by method of inclusion in proposal_hash), you can make the necessary updates to the protocol without invalidating the chain up to that point.
Though currently a permissioned blockchain, in the future there is potential to work on an open and decentralized variant of The X-Chain.
7. Further Pros and Cons of this Hybrid method:
Although Increased security at a smaller operational scale and higher throughput are the targeted benefits, this network offers other significant advantages, which are the side effects of centralization:
- Customizable Privacy. Transaction contents can be hidden, only the hash needs be shared openly.
- Interoperability with other chains requires a gas fees to be paid for on-ramp and off-ramp. From launch (June 2021), The X-Chain will be interoperable with XCUR ERC-20 and BSC-20.
- Low Latency, as known peers can be distributed in an optimized manner.
- Centralized control means fast response to problems in the network, such as voting to blacklist a hacker.
- Less Resources, used as the network doesn’t rely on PoW, which is a good thing both economically and environmentally.
- No need for transaction fees as rewards. The only reason for transaction fees is spam prevention, (which can be prevented through a transaction PoW system), or to generate revenue from the networks operation.
However, the model is not without its faults: Arguably, it is less secure than a massively distributed PoW network like bitcoin. This is a very centralized model as known peers control the mechanisms of the creating and committing blocks; centralization is always a security concern, although the distributed and polymorphic nature of the networks peers, mitigates some of that concern.
8. Attacks
Endorser Corruption — If an Endorser is individually hacked and their private key stolen, the hacker can approve false blocks or reject valid blocks. However the network would still run without a problem, as the majority of peers are still honest (Even if the Orderer is hacked), and those faulty blocks will not be added. Once the faulty node is detected, you can blacklist its public key from the list of known peers and replace it with a new (honest) one.
Consolidation Attack — This is a theoretical attack, whereby a malicious entity gains the private keys of at least X known peers. From this point they could consolidate/unify the public keys to a single local environment and recreate the blockchain from any point, with new data, and without any network delay. The exclusion of any network latency would mean that more blocks could be recreated within a given time. However, the inclusion of the hybrid’s PoW, is a significant barrier to altering history. This protection can be estimated as a function of the average hash strength of network and the number of blocks to be changed.
Further problems exists in the form of ‘denial of service’ attacks, primarily targeting the orderer. Sending ‘spam’ message to block a peers network connection will prevent them from engaging with the network. Considering each peer machine will have a list of all other peers, if one peer is attacked then there is a high chance to a DoS attack. However such an attack will halt the blockchain rather than change the data within it.
9. Summary
In summary, private networks must take advantage of their known peers to achieve some level of security. The launch of own hybridization blockchain, The X-Chain blockchain, is a step in the right direction, replacing the demand on proof of work and providing a scalable gasless platform.
Coming June 2021, alongside and integrated within our NFT Marketplace App.




